Crypto adoption is soaring in 2025, but so are the risks. As more people buy digital assets, cybercriminals are getting craftier—so a rock-solid crypto security checklist isn’t just smart, it’s essential. Whether you’re investing for the first time or managing a diverse portfolio, these practices are your first line of defense against hacks and scams.

1. Store Crypto in Hardware Wallets & Secure Your Seed Phrase
The golden rule? Never leave large amounts of crypto on exchanges. Hardware wallets (also called cold wallets) like Ledger or Trezor keep your coins offline—out of reach for hackers lurking online. But the wallet alone isn’t enough: your backup seed phrase is the master key to your funds. Write it down on paper (never digitally!) and hide it somewhere only you trust, such as a safe deposit box.
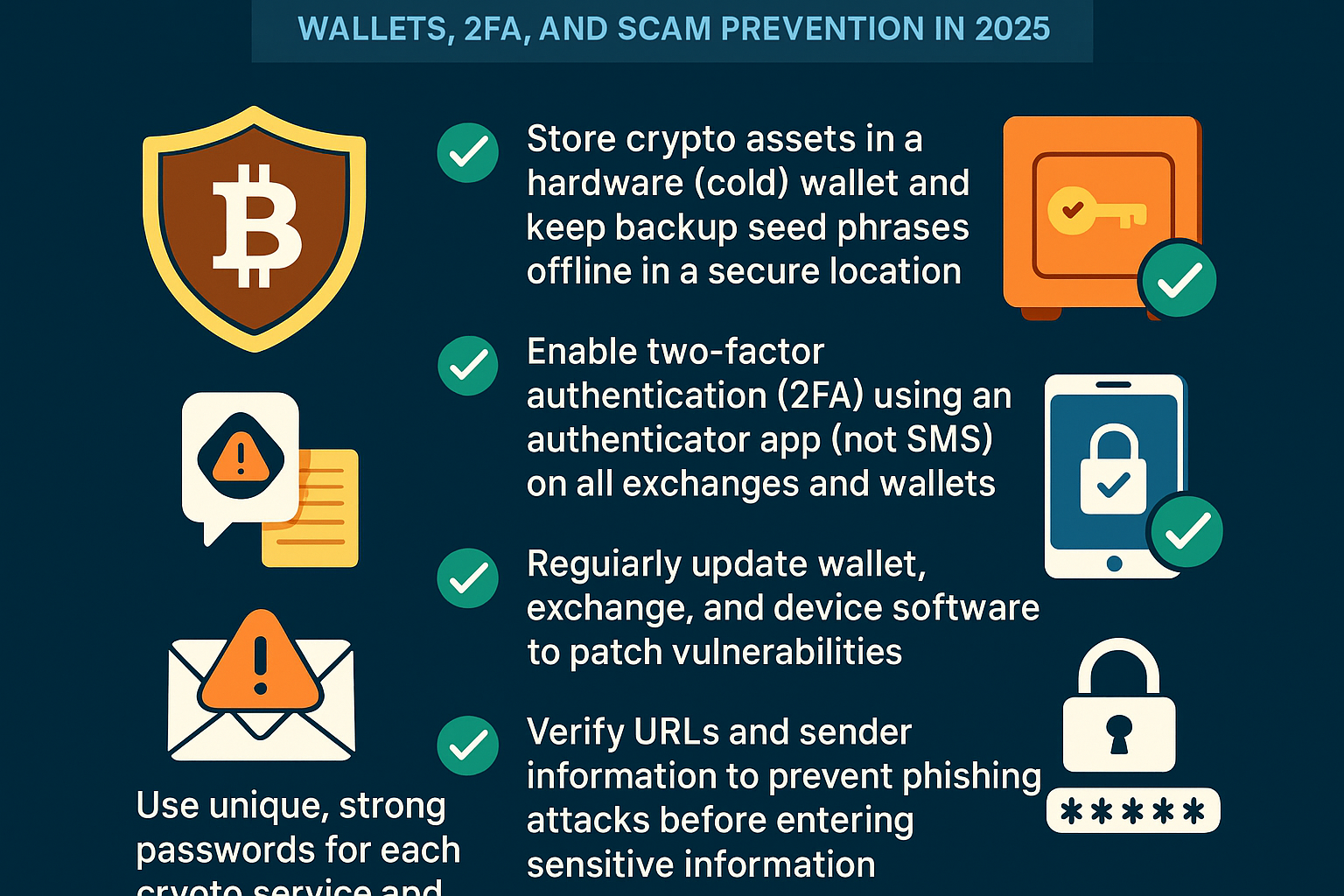
Essential Crypto Security Checklist for 2025
-

Store crypto assets in a hardware (cold) wallet and keep backup seed phrases offline in a secure location. Devices like Ledger Nano X or Trezor Model T provide robust protection against online threats. Always write down your seed phrase on paper and store it somewhere only you can access—never online or in cloud storage.
-
Enable two-factor authentication (2FA) using an authenticator app (not SMS) on all exchanges and wallets. Apps like Google Authenticator and Authy offer a much higher level of security than SMS-based 2FA, which is vulnerable to SIM swapping attacks.
-
Regularly update wallet, exchange, and device software to patch vulnerabilities. Stay current with the latest versions of your crypto wallets (such as Exodus or MetaMask), exchange apps (like Coinbase), and your operating system to ensure security patches are applied promptly.
-
Verify URLs and sender information to prevent phishing attacks before entering sensitive information. Double-check website addresses for exchanges like Binance or Kraken, and scrutinize emails for suspicious links or requests. Bookmark official sites and use browser extensions like MetaMask’s phishing detector for added safety.
-
Use unique, strong passwords for each crypto service and consider a reputable password manager. Tools like 1Password or Bitwarden help generate and store complex passwords, reducing the risk of credential reuse and account compromises.
2. Enable Two-Factor Authentication (2FA) — But Not With SMS
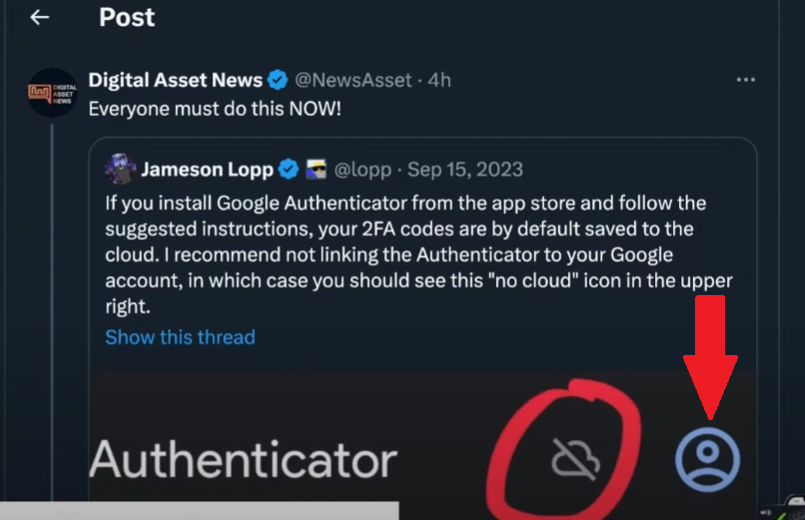
In 2025, relying on passwords alone is asking for trouble. Always enable two-factor authentication (2FA) on every exchange and wallet you use. But here’s the catch: skip SMS-based 2FA—it’s vulnerable to SIM swapping attacks! Instead, use an authenticator app like Google Authenticator or Authy for a much stronger layer of protection.
3. Keep Software Up-to-Date — Always
Your wallet software, exchange apps, even your phone’s OS—all need regular updates. Why? Because cyber attackers are constantly probing for new vulnerabilities, and developers race to patch them. Turn on automatic updates wherever possible. One overlooked update could be all an attacker needs to strike.
The Modern Crypto Security Mindset
The days of “set it and forget it” are over when it comes to digital assets. In this new era, proactive vigilance is everything—because threats evolve fast! The next half of our checklist covers phishing traps, password strategy, and advanced scam prevention tactics that every buyer should master.
4. Outsmart Phishing Attacks Every Time
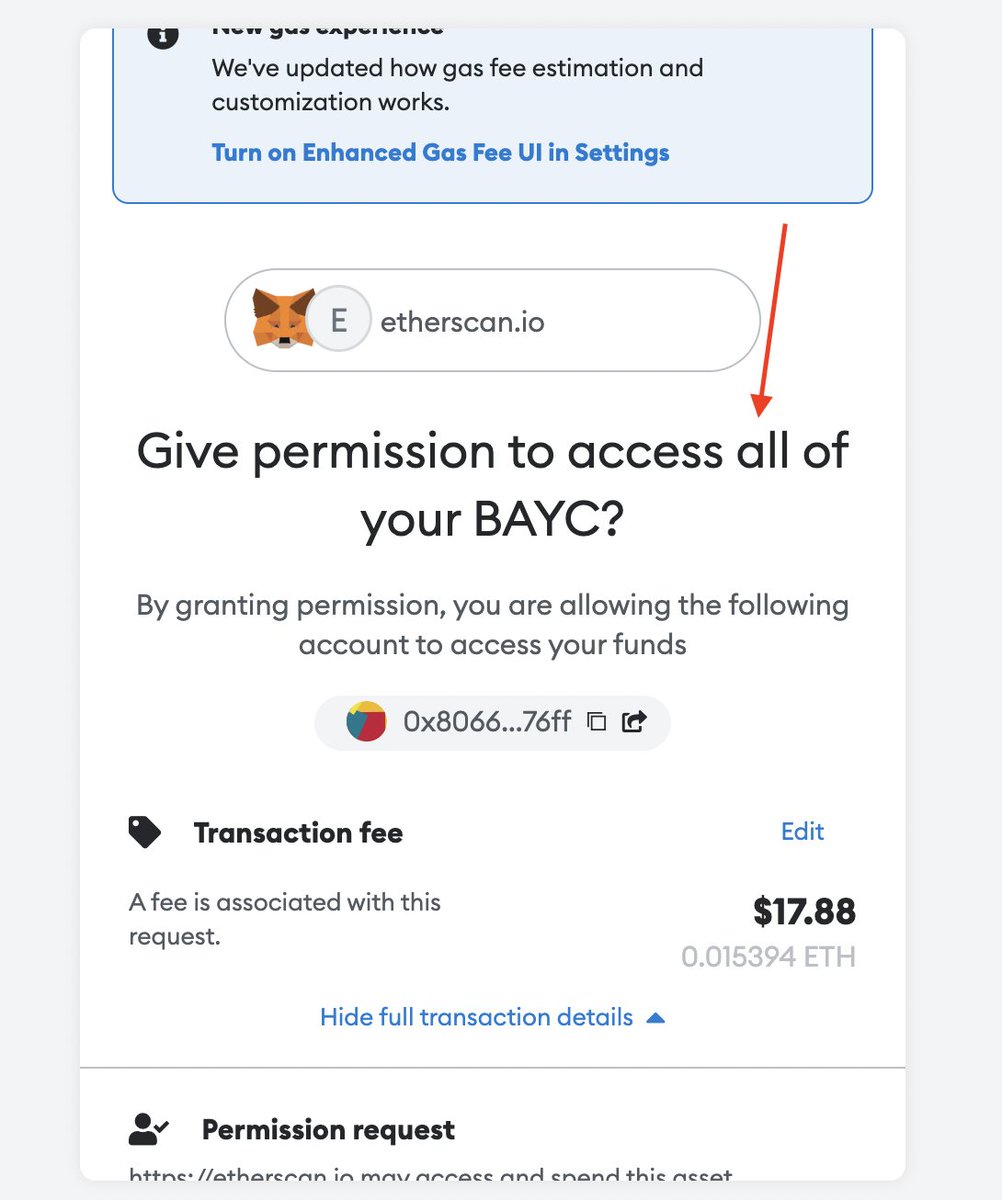
Phishing is still the number one way crypto investors get robbed in 2025. Hackers craft ultra-realistic fake websites and emails, hoping you’ll slip up and enter your credentials. Before entering sensitive info anywhere, triple-check the URL—even a single swapped letter can mean disaster! Always verify sender information in emails and never click on links from unknown sources. Bookmark your exchange and wallet sites, and access them directly instead of through search engines or email links.
Community vigilance is powerful—many scams are outed first on social media. Stay plugged into alerts from trusted crypto Twitter accounts and Discord channels to spot new threats as they emerge.
5. Upgrade Your Password Game
If you reuse passwords or stick with something easy to remember, you’re playing with fire. Create unique, strong passwords for every wallet and exchange. A reputable password manager can generate complex combinations you’d never memorize—and store them securely. This step alone thwarts most brute-force attacks that rely on leaked or reused credentials.
Stay Ahead: Make Security a Habit
Crypto security isn’t a one-and-done task—it’s an ongoing practice. Schedule regular security audits: check your backup seed phrase location, review 2FA settings, update apps, rotate passwords, and scan for phishing attempts monthly. Treat your digital assets like real-world valuables—because that’s exactly what they are.
The best time to level up your security was yesterday; the next best time is now.
As we look ahead to the future of decentralized finance, remember: your vigilance is your vault. The right habits today will keep your crypto safe—and empower you to explore all the opportunities this revolutionary space has to offer.